What are Social Engineering Attacks and How to Prevent Them?
by
7-layers of Security for Your WordPress Site
Your website needs the most comprehensive security to protect it from the constant attacks it faces everyday.

The weakest link in your website’s security is… you!
And other users as well, but mainly you.
Don’t believe us? Here’s a compelling stat: a staggering 74% of all data breaches involve a human element. And these breaches often take place through social engineering tactics.
Have you ever received an email that seemed urgent, but something about it felt off? Or perhaps you’ve received a call from “tech support” asking for your password?
If you answered ‘yes’, then you’ve encountered social engineering in action. Social engineering attacks exploit human behavior, making them one of the most insidious threats in cybersecurity today.
TL;DR: Social engineering attacks manipulate human behavior to steal sensitive information, affecting both individuals and organizations. Understanding these tactics and adopting preventive measures can significantly reduce the risk of falling victim to such attacks.
But here’s the good news: you can protect yourself. By understanding how social engineering works and adopting preventive measures, you can avoid becoming another statistic. In this article, we’ll explore different types of social engineering attacks, how they exploit human psychology, and, most importantly, how you can defend against them.
What is social engineering?
Social engineering tricks people into breaking normal security procedures to access sensitive information. Instead of exploiting software vulnerabilities, social engineers exploit human psychology. Imagine a burglar sweet-talking their way past a security guard instead of breaking a lock—that’s social engineering in action.
The roots of social engineering can be traced back to classic cons and scams. Think of the long con or the infamous Frank Abagnale, whose story was popularized in the movie Catch Me If You Can. These old-school tactics have simply evolved with technology.
In today’s digital age, social engineering attacks can come from phone calls, emails, social media interactions, and face-to-face encounters. Attackers use every tool at their disposal to deceive their targets. The exponential growth of the internet, smartphones, and computers has made it easier than ever for attackers to gather information and launch their schemes.
From tricking you into clicking a malicious link in an email to impersonating a colleague on social media, social engineering constantly adapts to new technologies and communication channels.

The problem is alarmingly widespread. For instance, in the 2013 Target data breach, attackers used a simple phishing email to gain access, leading to the theft of credit card details for over 40 million customers. It’s not just big corporations at risk; individuals can also fall prey to identity theft and financial loss from these schemes.
This might agitate you, and rightly so. Social engineering attacks bypass sophisticated security systems by targeting the weakest link in the chain: humans. Imagine the stress and anxiety of discovering your personal information has been stolen, or the fallout of a company-wide breach caused by a single deceptive email. The emotional and financial toll can be devastating.
Understanding social engineering tactics is the first step in protecting yourself.
How can you protect yourself and your visitors from social engineering attacks?
Protecting yourself and your website visitors from social engineering attacks requires a multi-layered approach, combining education, verification, and robust security measures. Here are some steps you can take:
Educate yourself and your visitors
Awareness is the first line of defense. Educate yourself and your website visitors about common social engineering attacks. Share tips and resources on how to recognize phishing emails, suspicious phone calls, and dubious social media messages. Knowledge empowers everyone to identify and avoid potential threats.
Verify, and re-verify identities
Always verify and re-verify the identities of anyone who contacts you or your visitors, especially if they request sensitive information. If someone claims to be from a trusted source, use known contact methods to confirm their identity independently. Never take identity claims at face value.
Use strong passwords
Encourage the use of strong, unique passwords and remind your website visitors to change them regularly. A good password is often a combination of uppercase and lowercase letters, numbers, and special characters. Implement password strength requirements on your site to enforce this practice.

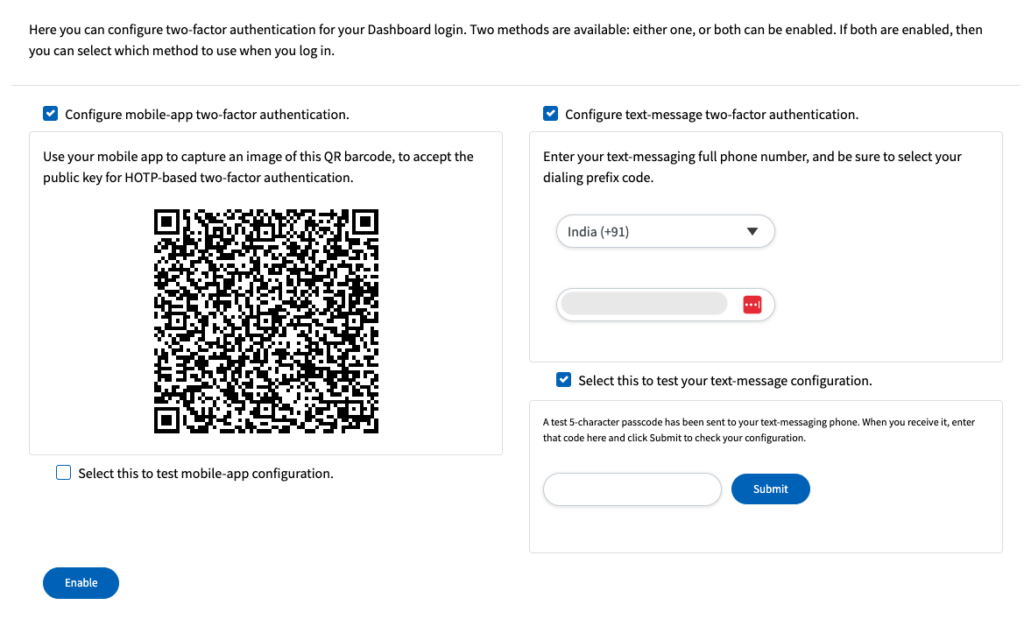
Enable two-factor authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security to your site. This mechanism requires an additional verification step, such as a code sent to a mobile device, making unauthorized access even more difficult.
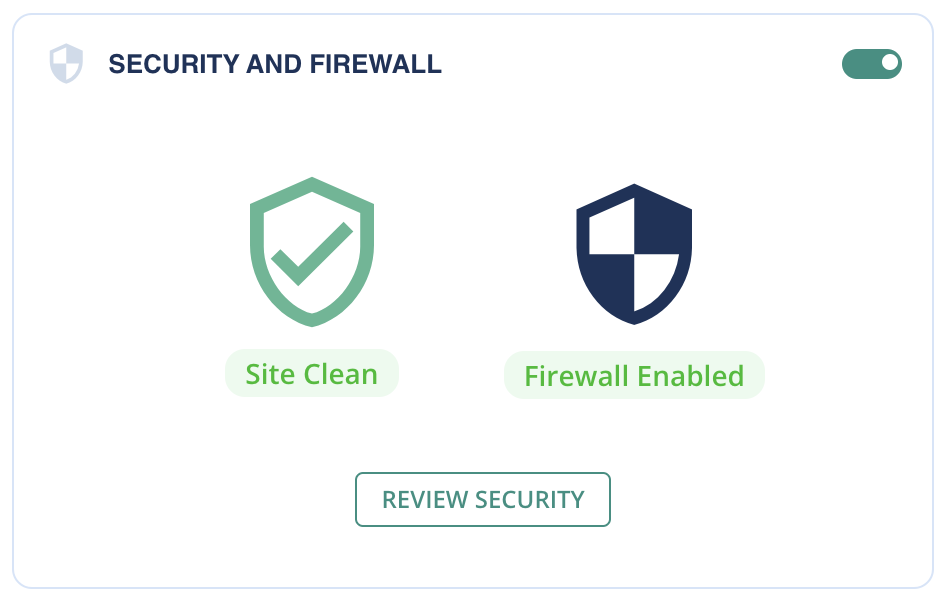
Add a security plugin like MalCare
Security plugins can provide substantial protection for your site. Consider adding a plugin like MalCare, which offers automatic malware scanning, firewall protection, and login protection. In case an account is compromised, and malware is injected into the site, MalCare will let you know if and when that happens. Such plugins can detect and block suspicious activity, providing an additional safeguard against social engineering attacks.
Regularly update all site-related software
Keep your website’s software, including content management systems, themes, and plugins, up to date. Regular updates ensure that you have the latest security patches and reduce vulnerabilities that attackers could exploit.
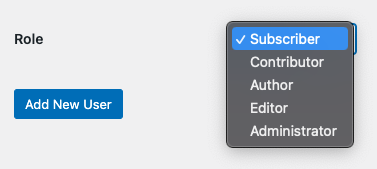
Limit access
Implement the principle of least privilege by limiting access to your site on a need-to-have basis. Only allow access to users who need it to perform their roles. This minimizes the number of potential entry points for attackers.
Encourage reporting
Create an environment where users feel comfortable reporting any potential social engineering attack. Provide easy ways for them to report suspicious emails, phone calls, or activities on your site. Prompt reporting can help you take swift action to mitigate threats.
What are some types of social engineering attacks?
Social engineering attacks come in various forms, each exploiting human psychology in unique ways. Understanding these types can help you recognize and avoid falling victim to them. Here’s a breakdown of some common social engineering attacks:
Phishing, spear phishing, and whaling
Phishing involves sending fraudulent emails or messages that appear to come from legitimate sources to trick recipients into revealing personal information or clicking malicious links. A more targeted form of this is spear phishing, where attackers customize their messages to specific individuals or organizations.
On the other hand, whaling is a form of phishing that targets high-profile individuals like executives or senior management, aiming for larger rewards.
An example of phishing would be an email claiming to be from your bank asking you to verify your account details by clicking on a link. To make it more convincing, it could be addressed to you by name and mention details relevant to your job or activities.

Smishing
Smishing uses SMS or text messages to deceive individuals into revealing personal information or clicking on malicious links. A text message claiming you’ve won a prize and asking you to click a link to claim it is an example of this type of attack.
Vishing
Vishing involves phone calls where attackers pose as legitimate entities to extract personal information. A caller pretending to be from your credit card company, asking for your card details to “verify” suspicious activity, is an example of vishing.
Baiting
Baiting creates enticing offers or situations to lure victims into a trap. For example, if an attacker leaves an infected USB drive labeled “Confidential” in a public place, some curious individual will eventually plug it into their computer. This can be significantly damaging if the individual were to do it on their work computer.
Quid-pro-quo
Quid-pro-quo offers a service or benefit in exchange for information. For example, a fake tech support call may offer to fix an issue in exchange for login credentials.
Piggybacking/tailgating
Piggybacking or tailgating refers to gaining unauthorized physical access by following someone with legitimate access into a secure area. In this attack, an attacker will closely follow an employee into a restricted area, claiming they forgot their access card, and gain access to the area.
Pretexting
Pretexting involves creating a fabricated scenario to obtain information or access. For example, an attacker could pose as an IT support staff asking for login credentials to fix a non-existent issue.
Business email compromise (BEC)
BEC involves compromising legitimate business email accounts to conduct unauthorized transfers or steal sensitive information. For example, an email from a compromised executive account directs the financial team to transfer funds to a new vendor.
Honeytraps
Honeytraps use romantic or flirtatious interactions to lure victims into divulging sensitive information. For example, an attacker may create a fake online profile to entice someone into sharing confidential details.
Scareware
Scareware frightens victims into downloading malicious software by presenting alarming messages. Pop-up ads that claim your computer is infected and urge you to download a fix, which is actually malware, is an example of scareware.
Watering hole attacks
These attacks compromise a website frequented by the target audience to deliver malware. For example, an attacker might infect a popular industry forum with malware, knowing that members of a specific company often visit the site.
What are the effects of social engineering attacks?
Social engineering attacks can have severe consequences, affecting various aspects of both personal and organizational life. Understanding these effects can underscore the importance of staying vigilant and employing robust security measures.
Identity theft
Identity theft is one of the most direct and personal impacts of social engineering attacks. When attackers gain access to personal information such as Social Security Numbers, birth dates, or financial details, they can use this data to impersonate victims. This can result in fraudulent transactions, opening new accounts in the victim’s name, and a lengthy, often grueling, process to reclaim one’s identity.
Data breaches
Data breaches occur when attackers use social engineering tactics to infiltrate an organization’s network and access sensitive data. This can include customer information, proprietary corporate data, and intellectual property. Breaches can lead to significant financial penalties, legal repercussions, and loss of trust from customers and partners.

Financial loss
Financial loss can result from both direct and indirect consequences of social engineering attacks. Direct losses occur when attackers trick victims into transferring money or providing financial information. Indirect losses can stem from dealing with the aftermath of an attack, such as legal fees, fines, and the cost of implementing better security measures.
Emotional and psychological impact
The emotional and psychological impact of social engineering attacks can be profound. Victims often experience feelings of violation, stress, anxiety, and a loss of trust in digital communications. For some, the strain can affect mental health, relationships, and overall well-being.
Reputational harm
Reputational harm can be devastating for organizations. A publicized security breach can erode trust and damage relationships with customers, partners, and stakeholders. Rebuilding a damaged reputation takes time and considerable effort, and some businesses may never fully recover.
Operational disruption
Operational disruption occurs when social engineering attacks compromise critical business functions and processes. Ransomware attacks, phishing scams that disrupt workflows, and unauthorized access to key systems can halt operations, leading to downtime and lost productivity.
How does social engineering work?
Social engineering capitalizes on human emotions and behaviors to exploit vulnerabilities. Attackers use a blend of technical skills and a deep understanding of psychology and social interactions to manipulate their targets effectively.
Some of the commonly exploited emotions are:
By understanding and exploiting these common human emotions, attackers create scenarios that feel real and believable to their targets. They might spend time researching their victims, learning their habits, and tailoring their strategies to appear as legitimate as possible.
To mount a successful social engineering attack, attackers go through the following four stages:
- Information gathering: In this phase, attackers collect data about their target to make their attack more convincing. They aim to understand the target’s habits, connections, and vulnerabilities.
- Relationship development: This phase involves establishing contact and building trust with the target. Attackers use the information gathered to craft believable scenarios and initiate interactions.
- Exploitation: In this phase, the attacker leverages the relationship and trust built to manipulate the target into performing actions or divulging sensitive information. This stage exploits common human emotions and psychological triggers.
- Execution: This phase involves completing the attack while minimizing suspicion and covering the attacker’s tracks. The goal is to ensure the target remains unaware that they have been manipulated.
The blending of technical skills with psychological insight makes social engineering particularly dangerous. The attacker’s goal is always the same: to manipulate their victim into giving up information or access they wouldn’t normally share.
Final thoughts
Social engineering attacks rely on manipulation rather than technical exploits, making them particularly insidious and effective. By understanding how these attacks work and recognizing the psychological tactics they use, you can better prepare yourself to defend against them.
Staying vigilant, staying informed, and always questioning what seems too good—or too urgent—to be true is the foundation of preventing social engineering attacks. Remember, the first step to cybersecurity is awareness. So safeguard yourself against such attacks with this simple motto: be skeptical, verify, and then trust.
FAQs
What is the 4 attack cycle of social engineering?
The 4 attack cycle of social engineering consists of four phases that an attacker goes through to mount an attack. These phases are information gathering, relationship development, exploitation, and finally, execution.
How does social engineering differ from traditional hacking?
Traditional hacking focuses on exploiting technical vulnerabilities in software or hardware, while social engineering relies on manipulating human behavior and emotions to access sensitive information or systems. Think of it as tricking someone into opening the front door rather than picking the lock.
Why are social engineering attacks effective?
Social engineering attacks are effective because they exploit common human traits such as trust, fear, curiosity, greed, and empathy. People are often more inclined to trust what appears to be a legitimate request, especially if it comes from a seemingly authoritative or familiar source.
What should I do if I suspect a social engineering attempt?
If you suspect a social engineering attempt, do not respond or click on any links. Verify the request through a known and trusted method, such as contacting the person or organization directly using official contact information. Report the incident to your IT department or the appropriate security team immediately.
Category:
Share it:
You may also like

MalCare Defends Against Login/Signup Popup Privilege Escalation Vulnerability
Imagine realizing that your once-secure office building, with restricted access to only trusted personnel, is now accessible to unauthorized individuals who have the same executive privileges as you! Now, imagine…

What are the Different Types of Website Logs?
Imagine driving a car without knowing your speed, engine temperature, or fuel levels. Sounds terrifying, right? Well, managing a website without understanding website logs is a bit like that. You…

What is Cross-Site Scripting (XSS) and How to Prevent It?
Websites can sometimes act strangely, showing unexpected pop-ups or exposing personal information. This isn’t just a glitch—it’s often due to a sneaky trick called Cross-Site Scripting (XSS). You might be…
How can we help you?
If you’re worried that your website has been hacked, MalCare can help you quickly fix the issue and secure your site to prevent future hacks.

My site is hacked – Help me clean it
Clean your site with MalCare’s AntiVirus solution within minutes. It will remove all malware from your complete site. Guaranteed.

Secure my WordPress Site from hackers
MalCare’s 7-Layer Security Offers Complete Protection for Your Website. 300,000+ Websites Trust MalCare for Total Defence from Attacks.








